IMSI Catcher System
Is a powerful cellular interception tool designed to help law enforcement agencies covertly collect mobile identities such as IMSI and IMEI from nearby mobile phones, without alerting service providers or phone users.
IMSI Catcher System silently collecting mobile phone identities from 2G, 3G, 4G, and 5G (NSA) networks. These systems help identify and locate targets by scanning all active mobile networks in the area.
Once a device is detected, the system logs essential details like:
- IMSI
- IMEI
- TMSI (Temporary Mobile Subscriber Identity)
- Location and PLMN information

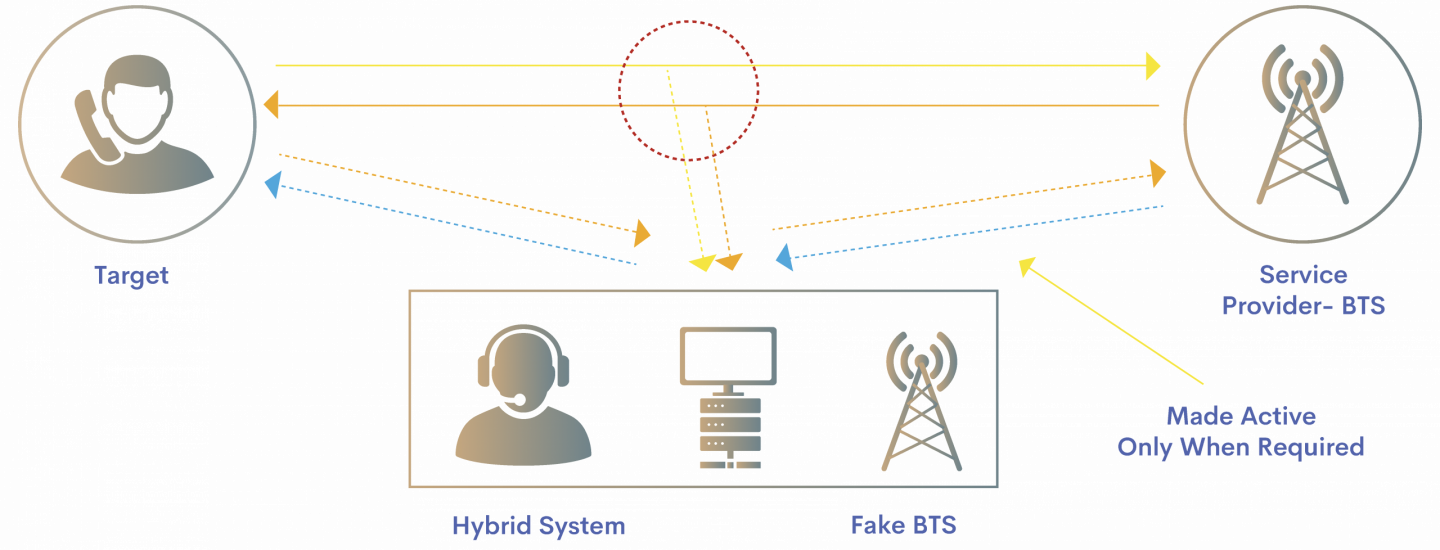
Tactical cellular monitoring solution for intercepting voice calls, SMS, and data traffic. GM Active is an advanced version of IMSI Catcher that allows you to intercept and manipulate all incoming and outgoing communications of mobile phones in range, including voice calls, SMS, data traffic, USSD commands.

An IMSI Catcher is specialized surveillance equipment designed to collect identities (such as IMSI and IMEI) of mobile phones in range. GM Catcher steps beyond the basic IMSI/IMEI collection and offers a comprehensive set of functionalities – such as detecting a mobile phone number (MSISDN) and utilizing our GM Gates OSINT solution to reveal meaningful insights about the target.

Broadcasting solution for SMS and emergency alert messages GM Message is a robust solution for broadcasting messages to mobile subscribers in the vicinity. It supports three different types of messages, including cell broadcast.

Passive cellular monitoring solution with A5.3 decryption. GM Passive is designed for passive real-time monitoring of voice calls, SMS messages, and USSD codes in GSM networks. To operate with network providers using A5.3 encryption, GM Passive can be equipped with an optional downgrader module, which enables the downgrade of A5.3 communications to A5.1
Intercept Phone
Cellular Interception Solution help law enforcement authorities to acquire analyse and manage intercepted cellular communications such as voice and data.This becomes vital as terrorist and criminal elements rely upon cellular mobile communications to carry out their nefarious operations.